#Multi-cloud managed services
Explore tagged Tumblr posts
Text
Our multi-cloud managed services offer a strategic approach to optimizing cloud operations, enhancing flexibility, and improving cost efficiency. By leveraging a comprehensive multi-cloud strategy, we help businesses reduce risks, achieve high availability, and streamline management across diverse cloud environments. Our services include expert advisory, seamless migration, cost management, and robust security measures to ensure your cloud infrastructure supports business growth and adapts to changing needs. Explore how our solutions can transform your cloud operations and drive greater resilience and efficiency.
0 notes
Text
#Backup and Restore Tools#backup strategies#Cloud Storage for MSPs#Data Security#Data Transfer Solutions#managed service providers#MSP backup solutions#Multi-Location Backups#Ransomware Protection#Secure Data Backups
0 notes
Text
At DVS IT Services, we specialize in Linux Server Management, Cloud Migration, Data Center Migration, Disaster Recovery, and RedHat Satellite Server Solutions. We also offer expert support for AWS Cloud, GCP Cloud, Multi-Cloud Operations, Kubernetes Services, and Linux Patch Management. Our dedicated team of Linux Administrators helps businesses ensure smooth server operations with effective root cause analysis (RCA) and troubleshooting. Learn more about our services at https://dvsitservices.com/.
#At DVS IT Services#Linux Server Management#Cloud Migration#Data Center Migration#Disaster Recovery#RedHat Satellite Server Solutions.#GCP Cloud#Multi-Cloud Operations#Kubernetes Services
0 notes
Text
Enhance Your Security with MFA!

As part of Cybersecurity Awareness Month, Century Solutions Group is emphasizing the importance of using Multi-Factor Authentication (MFA) to keep your accounts secure.
Why MFA Matters: MFA adds an extra layer of protection by requiring multiple forms of verification, making it much harder for attackers to gain access to your accounts. Even if your password is compromised, MFA ensures that additional verification steps are needed.
Tips on Using MFA:
-Enable MFA on all your accounts: This includes email, social media, banking, and any other accounts that support it.
-Use a combination of factors: Something you know (password), something you have (smartphone or token), and something you are (fingerprint or facial recognition).
-Regularly update your MFA settings: Ensure your contact information is up-to-date and review your MFA methods periodically.
Choosing the Best MFA App:
-Look for strong encryption: Ensure the app offers robust encryption to protect your data.
-Check for compatibility: The app should work across all your devices and platforms.
-Consider additional features: Look for apps that offer features like backup options, biometric authentication, and easy recovery processes.
Stay tuned for more tips throughout the month to help you "Secure Our World"! https://centurygroup.net/cloud-computing/
#CybersecurityAwarenessMonth #SecureOurWorld #CenturySolutionsGroup #StaySafeOnline
#Cybersecurity#Cybersecurity Awareness Month#Cloud Computing#managed it services#MFA#Multi Factored Authentication
1 note
·
View note
Text
Exclusive Webinar | CloudLeap & Merino Consulting Services Present Infor LN Integrated Global Shipping Solutions.
We’re excited to remind you that our highly anticipated webinar is just around the corner! Get ready to explore game-changing features designed to elevate your logistics operations:
🔹Address Validation: Eliminate costly address correction fees by ensuring precise delivery information.
🔹 Rate Shopping & Business Rules: Effortlessly compare carrier rates and automate decision-making with customized business rules.
🔹 Ocean Container Tracking: Achieve end-to-end visibility on your shipments for improved transparency and control.
These are just a few of the powerful capabilities we’ll dive into. Don’t miss out on transforming your shipping processes and driving efficiency!
📅 USA: October 23rd, 2024
🕒 2:00 PM - 3:00 PM EDT
👉 Register now
https://cloudleap.com

#shipping software#shipping solutions#logistics software#multi carrier shipping software#cloud shipping#supply chain#shipping system#tracking software#ecommerce#Webinar#Piyovi#CloudLeap#Merino Consulting Services#Infor LN#transportation management software
0 notes
Text
Elevate Your IT Infrastructure with Sify's Multi Cloud Managed Services
In today’s digital era, the agility and scalability offered by cloud computing are indispensable for businesses aiming to stay competitive and innovative. However, managing multiple cloud environments can be complex and resource-intensive. Sify’s Multi Cloud Managed Services are designed to simplify and optimize your cloud strategy, allowing your organization to harness the full potential of multi-cloud environments with ease and efficiency.
Unmatched Flexibility and Scalability
Sify’s Multi Cloud Managed Services provide the flexibility to leverage multiple cloud platforms, including public, private, and hybrid clouds, tailored to your specific business needs. This approach ensures that you can choose the best solutions for different workloads, enhancing performance, cost-efficiency, and scalability.
Seamless Integration and Management
Sify seamlessly integrates various cloud environments into a unified management framework. This enables you to manage all your cloud resources from a single pane of glass, simplifying operations and reducing the complexity of multi-cloud management.
Optimized Performance and Cost Efficiency
With Sify’s expertise, you can optimize the performance of your multi-cloud environment by ensuring that each workload is deployed on the most suitable platform. This not only enhances performance but also maximizes cost efficiency, ensuring that you get the best return on your cloud investment.
Comprehensive Cloud Services
Sify’s Multi Cloud Managed Services encompass a wide range of offerings designed to meet the diverse needs of modern enterprises. From strategy and planning to implementation and ongoing management, Sify provides end-to-end services that ensure your cloud environment is always aligned with your business objectives.
Cloud Strategy and Planning
Sify collaborates with your organization to develop a comprehensive cloud strategy that aligns with your business goals. This includes assessing your current IT infrastructure, identifying suitable cloud platforms, and designing a roadmap for seamless cloud adoption and migration.
Cloud Migration
Transitioning to a multi-cloud environment can be challenging, but Sify’s cloud migration services make it smooth and hassle-free. Sify ensures minimal disruption to your operations while migrating your applications and data to the cloud, maintaining data integrity and security throughout the process.
Cloud Management and Optimization
Sify’s ongoing management services include monitoring, maintenance, and optimization of your cloud resources. By continuously analyzing your cloud environment, Sify identifies opportunities for cost savings and performance improvements, ensuring that your cloud infrastructure remains efficient and effective.
Security and Compliance
Security is a top priority in any cloud strategy. Sify’s comprehensive security solutions protect your cloud environment from potential threats and ensure compliance with industry regulations. From data encryption and identity management to threat detection and response, Sify provides a multi-layered security approach that safeguards your critical assets.
Empowering Innovation with Sify’s Expertise
Partnering with Sify for your multi-cloud journey means leveraging the expertise and experience of a leading provider in the cloud services industry. Sify’s team of certified cloud professionals brings deep knowledge and insights to every project, ensuring that your cloud environment is optimized for success.
Certified Cloud Professionals
Sify’s team comprises certified experts with extensive experience in managing multi-cloud environments. Their expertise ensures that your cloud strategy is implemented with precision and that your cloud resources are managed effectively.
Customer-Centric Approach
Sify’s customer-centric approach means that your unique needs and challenges are always at the forefront. Sify works closely with your organization to understand your business objectives and tailor solutions that meet your specific requirements.
Proven Track Record
With a proven track record of successful multi-cloud deployments, Sify is a trusted partner for businesses worldwide. Sify’s commitment to excellence and innovation ensures that your multi-cloud environment will drive business growth and transformation.
In an increasingly dynamic and competitive business landscape, the ability to effectively manage multiple cloud environments is crucial for success. Sify’s Multi Cloud Managed Services provide the comprehensive solutions you need to navigate the complexities of multi-cloud management, optimize performance, and ensure security and compliance. With Sify as your partner, you can focus on driving innovation and achieving your business goals while Sify takes care of your cloud infrastructure. Elevate your IT infrastructure with Sify’s Multi Cloud Managed Services and unlock the full potential of the cloud.
0 notes
Text
Mastering the Multiverse: Sify's Multi-Cloud Managed Services
In the ever-evolving realm of cloud computing, the concept of multi-cloud has emerged as a beacon of flexibility and resilience, offering organizations the freedom to choose the best-of-breed solutions from multiple cloud providers. At the forefront of this transformative wave stands Sify, a trusted leader in technology solutions, delivering cutting-edge Multi-Cloud Managed Services that empower businesses to harness the full potential of their multi-cloud environments. With Sify’s expertise and dedication to excellence, organizations can navigate the complexities of multi-cloud with confidence and clarity.
Navigating the Multi-Cloud Landscape:
Sify understands that no two organizations are alike, each with its unique set of challenges, objectives, and aspirations. That’s why our Multi-Cloud Managed Services are designed to be adaptable, scalable, and tailored to meet the specific needs of each client. Whether you’re looking to leverage the scalability of AWS, the innovation of Azure, or the performance of Google Cloud Platform, Sify has the tools, expertise, and resources to support your multi-cloud journey every step of the way.
The Power of Multi-Cloud:
Multi-cloud architecture offers organizations the flexibility and agility to choose the right cloud services for each workload or application, optimizing performance, cost, and compliance. With Sify’s Multi-Cloud Managed Services, organizations can seamlessly integrate multiple cloud providers, applications, and environments, enabling greater flexibility, efficiency, and innovation.
Key Features and Benefits:
Comprehensive Management: Our Multi-Cloud Managed Services provide end-to-end management of your multi-cloud environment, from planning and deployment to ongoing optimization and support. With Sify as your trusted partner, you can focus on your core business objectives while we take care of the rest.
Seamless Integration: We understand the importance of seamless integration between multiple cloud providers. Our Multi-Cloud Managed Services enable organizations to seamlessly migrate workloads, applications, and data between clouds with minimal disruption.
Cost Optimization: Cost optimization is paramount in today’s competitive landscape. Our Multi-Cloud Managed Services help organizations optimize their cloud spend, ensuring that they get the most value out of their multi-cloud investment.
Security and Compliance: Security is our top priority. Our Multi-Cloud Managed Services include robust security measures and compliance controls to protect sensitive data and applications across multiple cloud environments.
Scalability and Flexibility: Whether you’re scaling up to meet growing demand or scaling down to reduce costs, our Multi-Cloud Managed Services scale seamlessly to meet your evolving needs. With pay-as-you-go pricing and flexible deployment options, you can adapt to changing business requirements with ease.
Unlock Multi-Cloud Excellence with Sify:
In an era of rapid digital transformation, having the right technology partner by your side is essential. With Sify’s Multi-Cloud Managed Services, organizations can unlock the full potential of multi-cloud and embark on a journey of innovation, agility, and growth. Join the ranks of leading organizations who trust Sify to deliver world-class multi-cloud solutions that drive results. Discover the power of Multi-Cloud Managed Services with Sify today.
0 notes
Text
Ansible vs Terraform: Best DevOps tool?
Ansible vs Terraform: Best DevOps tool? @vexpert #vmwarecommunities #homelab #ansiblevsterraform #cloudinfrastructuremanagement #provisioninginfrastructure #configurationmanagementtools #infrastructureascode #multiclouddeployment #networkautomation
Ansible and Terraform are excellent DevOps tools that can provide many automation benefits in enterprise and cloud environments. Both of them have capabilities that can overlap with each other. However, I would say that each has its strengths in configuring and provisioning infrastructure. Look at Ansible vs Terraform and see which automation tool is best for which task. Table of contentsAt a…

View On WordPress
#ansible vs terraform#automation tools comparison#Cloud Infrastructure Management#configuration management tools#immutable infrastructure approach#infrastructure as code#managing cloud services#multi-cloud deployment#network automation with ansible and terraform#provisioning infrastructure
0 notes
Text
Axolt: Modern ERP and Inventory Software Built on Salesforce
Today’s businesses operate in a fast-paced, data-driven environment where efficiency, accuracy, and agility are key to staying competitive. Legacy systems and disconnected software tools can no longer meet the evolving demands of modern enterprises. That’s why companies across industries are turning to Axolt, a next-generation solution offering intelligent inventory software and a full-fledged ERP on Salesforce.
Axolt is a unified, cloud-based ERP system built natively on the Salesforce platform. It provides a modular, scalable framework that allows organizations to manage operations from inventory and logistics to finance, manufacturing, and compliance—all in one place.
Where most ERPs are either too rigid or require costly integrations, Axolt is designed for flexibility. It empowers teams with real-time data, reduces manual work, and improves cross-functional collaboration. With Salesforce as the foundation, users benefit from enterprise-grade security, automation, and mobile access without needing separate platforms for CRM and ERP.
Smarter Inventory Software Inventory is at the heart of operational performance. Poor inventory control can result in stockouts, over-purchasing, and missed opportunities. Axolt’s built-in inventory software addresses these issues by providing real-time visibility into stock levels, warehouse locations, and product movement.
Whether managing serialized products, batches, or kits, the system tracks every item with precision. It supports barcode scanning, lot and serial traceability, expiry tracking, and multi-warehouse inventory—all from a central dashboard.
Unlike traditional inventory tools, Axolt integrates directly with Salesforce CRM. This means your sales and service teams always have accurate availability information, enabling faster order processing and better customer communication.
A Complete Salesforce ERP Axolt isn’t just inventory software—it’s a full Salesforce ERP suite tailored for businesses that want more from their operations. Finance teams can automate billing cycles, reconcile payments, and manage cash flows with built-in modules for accounts receivable and payable. Manufacturing teams can plan production, allocate work orders, and track costs across every stage.
86 notes
·
View notes
Note
Ohoho WIP Ask meme reading these WIPs has been a ton of fun!! I'd love to hear more about 8 and 9 🌟👀
^_^
8. Outshine the Sun
This one is the actual backstory-story, about Resh'an and Aephorul meeting and falling in love and studying alchemy together. It's an ambitious concept for me- slow burn, multi-chaptered, plotty, set over the backdrop of a fascist imperial state. Resh'an is an Imperial Alchemist and scholar at the University; Aephorul is a prince from a neighboring vassal state, technically still autonomous but in a politically tenuous situation. (Full disclosure, I only just recently watched Fullmetal Alchemist for the first time, so the actual parallels between this backstory and all of that are largely coincidental.) (Aephorul's kingdom eventually gets the Ishval treatment, though.)
The full scope of the story is beyond my skills to write, honestly, particularly since I keep being indecisive about major plot points. Most of what I've actually written at this point is just four or five variations on Aephorul's disastrous love confession, and Resh'an getting a concussion. (Those two events are related.)
What I may do eventually is try to break this down into more manageable chunks- a smaller story dealing with their first meeting and early friendship, a slightly longer thing dealing with the love confession disaster and their subsequent epistolary romance (which is really the part of the story I'm excited to tell, because I enjoy making everyone- myself, the characters, my readers- suffer). And then maybe a third story dealing with the fallout of the political situation/civil war, and their decision to pursue immortality.
Here's a tiny fragment from early on in the story.
----
He drew a circle in the sand. “The First Sphere: transmutation of the natural world. Chrysopoeia, sublimation of mercury, the forge master's steel. That's the alchemy we perform in the Emperor's service.”
Aephorul crossed his arms. “Hellfire and explosives. Poisons. The killing clouds.”
“Yes. We create those, too.” Aephorul was glaring at him. Resh'an met his glare without flinching. “We serve at the Emperor's command.”
“And if the Imperial armies marched on the frontier, would you still serve? You come running when Justice calls.”
“Your highness- what choice do you think I have? I'm a Scholar, not a warmage. But if the palace calls for me, I have to answer.” He twisted his hands in the sleeves of his robe. “If the Empire goes to war, the Imperial Alchemists will go where we are sent. The only way I'll ever leave Imperial service is on a funeral pyre.”
“It won't be a war,” Aephorul said softly. “That won't be necessary. The harvests will continue to fail. The Empire's grain will save us from starvation and empty the royal coffers, and- do you know the real reason I was sent here?”
“What?” Resh'an took a step back. Aephorul wasn't glaring now, but the look in his eyes was intense.
“There are plenty of wealthy, unmarried women in the capital. I'm of no real use to my family on the frontier- but if I can secure an advantageous marriage, then maybe I'll be worth something.” He crossed his arms. “The seneschal prefers that I keep my mouth shut while he finds me a likely prospect. Probably some widowed heiress who likes the idea of having a pet savage on a pretty leash.”
“Aephorul…” Resh'an touched his shoulder, hesitantly. Aephorul jerked his arm away.
“Keep your pity, Scholar,” he snarled.
“Of course, your highness,” he said acidly. “You seem to have plenty for yourself already.”
Aephorul startled at that, eyes widening in surprise. “So you do have teeth. Here I thought the University must have defanged you.”
Resh'an snorted. "I'll have you know the students at the Academy are terrified of me."
"What, the little ducklings that follow you around the Library with stars in their eyes?" Aephorul cracked a smile at last, and shook his head.
He met Aephorul's smile with a grin. "You've been following me around the Library, your highness." As soon as he said it, Resh'an wished he hadn't; it was one thing to befriend the prince, insofar as an indentured Scholar could befriend foreign royalty.
It was another thing entirely to flirt with him. Resh'an knew better. He cleared his throat, and gestured to the diagrams with his staff. "All those little ducklings pay attention in their classes, at least."
---
9. Game, Set, Match
I hate this title. I hate it! It has to change. I hated Loser Takes All, but that at least felt thematically appropriate given what happens, amd it's grown on me. Thats not the case here at all. Really, since this one is from Aephorul's pov, the title ought to have something to do with dreams, or longing. Resh'an's pov gets all the gaming metaphors.
Anyway, this is the direct sequel to Save Scumming; It's fairly lighthearted, relatively speaking, and is really just supposed to be some wacky porn. But I guess they do end up yelling at each other and crying about it a bit. Par for the course, really.
It takes place a decade or so after Save Scumming, or at least some interval of time that might feel long to a mortal but isn't unduly long for them. But for perspective- it's maybe 6-9 months from Loser Takes All through the end of Save Scumming. Part of the reason they're both so unhinged about everything is because prior to the events of Sea of Stars, they hadn't seen each other for a thousand years.
I'll be real here: my favorite part of this story is getting to do more weird inhuman/body horror things with Aephorul. Here's a taste:
---
He dug his other tentacles into the loam like a tree putting down roots. The mycelial network beneath the soil reached back- forests had souls, too, and this one was particularly ancient and vast. Older than both of them, by at least a full order of magnitude.
He rarely encountered living things that old, but perhaps that was why Resh'an had chosen this place. Aephorul held no particular reverence for such things, not anymore. He could have sunk his claws into the forest's soul and destroyed it, disrupting the careful balance of microbial life that was the foundation for every living system. He could inject plague into the lifeblood of this world, and watch it devour itself. But he'd made a deal. An entire continental forest system wasn't exactly minimal casualties.
So he acknowledged that vast and ponderous soul, and felt it acknowledge him in turn. He would only extract what he needed from the soil: calcium and phosphate; extra carbon and few other trace minerals. His flesh was all the alchemy equipment he needed here- he could synthesize bone in his sleep.
That was usually when he preferred to do it, honestly. It was always nice to wake up from a nap with a brand new set of knees.
12 notes
·
View notes
Text
Demystifying cloud computing: the future of technology.

In today's rapidly evolving digital world, cloud computing is not just a technology trend-cloud computing is the foundation of today's IT infrastructure. from streaming your favourite Netflix show to collaborating on Google Docs.
what is cloud computing?

Cloud computing is the provision of computing services including the servers, databases, storage, networking, software, analytics, and intelligence over the internet to offer faster innovation, flexible resources, and economies of scale.
Types of cloud services.
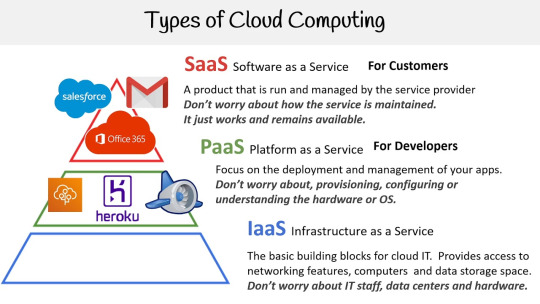
Security in the cloud.
Security is the top priority. cloud vendors employ encryption, firewalls, multi-factor authentication, and periodic audits to secure data. Organizations must, however, set up and manage secure access.
The future of cloud computing.

The future of cloud computing is being defined by a number of ground breaking trends that are changing the way data and applications are processed. Edge computing is moving computation near data sources to decrease latency and improve real-time processing for IoT and mobile applications.
7 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text

Welcome to Hyperloop Cloud Space having 15+ years of experience cloud and data center services! Our expertise in cloud computing and data center management ensures that your business stays ahead in todays fast-paced digital landscape. catering to 12k+ customers our datacenter. They include a range of solutions such as colocation, cloud hosting, disaster recovery, and Multi-Cloud Solutions such as AWS Cloud, Google Cloud, Azure Cloud services.
Hyperloop Cloud computing is characterized by on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service. These characteristics enable businesses to access computing resources quickly and easily, adapt to changing demands, and pay only for what they use.
#cloudcomputing#cloud hosting#tallyoncloud#tallyprimeawscloud#tallyawscloud#tallyprime#hyperloopcloud#vpsserver#dedicatedserver#privatecloud
2 notes
·
View notes
Text
The Role of CCNP in Multi-Cloud Networking
We live in a time where everything is connected—our phones, laptops, TVs, watches, even our refrigerators. But have you ever wondered how all this connection actually works? Behind the scenes, there are large computer networks that make this possible. Now, take it one step further and imagine companies using not just one but many cloud services—like Google Cloud, Amazon Web Services (AWS), and Microsoft Azure—all at the same time. This is called multi-cloud networking. And to manage this kind of advanced setup, skilled professionals are needed. That’s where CCNP comes in.
Let’s break this down in a very simple way so that even a school student can understand it.
What Is Multi-Cloud Networking?
Imagine you’re at a school event. You have food coming from one stall, water from another, and sweets from a third. Now, imagine someone needs to manage everything—make sure food is hot, water is cool, and sweets arrive on time. That manager is like a multi-cloud network engineer. Instead of food stalls, though, they're managing cloud services.
So, multi-cloud networking means using different cloud platforms to store data, run apps, or provide services—and making sure all these platforms work together without any confusion or delay.
So, Where Does CCNP Fit In?
CCNP, which stands for Cisco Certified Network Professional, teaches you how to build, manage, and protect networks at a professional level. If CCNA is the beginner level, CCNP is the next big step.
When we say someone has completed CCNP training, it means they’ve learned advanced networking skills—skills that are super important for multi-cloud setups. Whether it’s connecting a company’s private network to cloud services or making sure all their apps work smoothly between AWS, Azure, and Google Cloud, a CCNP-certified person can do it.
Why Is CCNP Important for Multi-Cloud?
Here are a few simple reasons why CCNP plays a big role in this new world of multi-cloud networking:
Connecting Different Platforms: Each cloud service is like a different language. CCNP helps you understand how to make them talk to each other.
Security and Safety: In multi-cloud networks, data moves in many directions. CCNP-certified professionals learn how to keep that data safe.
Speed and Performance: If apps run slowly, users get frustrated. CCNP training teaches you how to make networks fast and efficient.
Troubleshooting Problems: When something breaks in a multi-cloud system, it can be tricky to fix. With CCNP skills, you’ll know how to find the issue and solve it quickly.
What You Learn in CCNP That Helps in Multi-Cloud
Let’s look at some topics covered in CCNP certification that directly help with multi-cloud work:
Routing and Switching: This means directing traffic between different networks smoothly, which is needed in a multi-cloud setup.
Network Automation: You learn how to make systems work automatically, which is super helpful when managing multiple clouds.
Security: You’re trained to spot and stop threats, even if they come from different cloud platforms.
Virtual Networking: Since cloud networks are often virtual (not physical wires and cables), CCNP teaches you how to work with them too.
Can I Learn CCNP Online?
Yes, you can! Thanks to digital learning, you can take a CCNP online class from anywhere—even your home. You don’t need to travel or sit in a classroom. Just a good internet connection and the will to learn is enough.
An online class is perfect for students or working professionals who want to upgrade their skills in their free time. It also helps you learn at your own speed. You can pause, repeat, or review topics anytime.
What Happens After You Get Certified?
Once you finish your CCNP certification, you’ll find many doors open for you. Especially in companies that use multiple cloud platforms, your skills will be in high demand. You could work in roles like:
Cloud Network Engineer
Network Security Analyst
IT Infrastructure Manager
Data Center Specialist
And the best part? These roles come with good pay and long-term career growth.
Where Can I Learn CCNP?
You can take CCNP training from many places, but it's important to choose a center that gives you hands-on practice and teaches in simple language. One such place is Network Rhinos, which is known for making difficult topics easy to understand. Whether you’re learning online or in-person, the focus should always be on real-world skills, not just theory.
Final Thoughts
The world is moving fast toward cloud-based technology, and multi-cloud setups are becoming the new normal. But with more clouds come more challenges. That’s why companies are looking for smart, trained professionals who can handle the job.
CCNP training prepares you for exactly that. Whether you're just starting your career or want to move to the next level, CCNP gives you the skills to stay relevant and in demand.
With options like a CCNP online class, you don’t even have to leave your house to become an expert. And once you complete your CCNP certification, you're not just learning about networks—you’re becoming someone who can shape the future of cloud technology.
So yes, if you’re thinking about CCNP in a world that’s quickly moving to the cloud, the answer is simple: go for it.
2 notes
·
View notes
Text
https://www.sifytechnologies.com/cloud-services/multi-cloud-management-services/

Sify's Multi Cloud Managed Services: Navigating the Complexity of Cloud with Confidence
In the digital era, cloud computing has become a cornerstone for businesses looking to drive innovation, agility, and growth. However, as enterprises increasingly adopt multi-cloud strategies to leverage the unique benefits of various cloud providers, managing these diverse environments can become complex and challenging. Sify Technologies, a pioneer in Information and Communications Technology (ICT) solutions, offers comprehensive Multi Cloud Managed Services to help businesses seamlessly navigate the intricacies of multi-cloud environments, ensuring optimized performance, security, and cost-efficiency.
Unleashing the Power of Multi-Cloud
Sify’s Multi Cloud Managed Services are designed to unlock the full potential of multi-cloud environments. By integrating services from leading cloud providers such as AWS, Microsoft Azure, Google Cloud Platform, and others, Sify enables enterprises to select and combine the best solutions to meet their specific needs. This approach ensures that businesses can harness the strengths of each cloud platform, driving innovation and achieving their strategic objectives.
Seamless Integration and Management
One of the key challenges of a multi-cloud strategy is seamless integration and management across various cloud platforms. Sify’s team of cloud experts excels in designing and implementing multi-cloud architectures that ensure interoperability and seamless data flow between different environments. By leveraging advanced tools and automation, Sify simplifies the management of multi-cloud infrastructures, allowing businesses to focus on their core activities without worrying about the underlying complexities.
Enhanced Security and Compliance
Security and compliance are paramount in the multi-cloud landscape. Sify’s Multi Cloud Managed Services incorporate robust security measures to protect data and applications across all cloud environments. With a multi-layered security approach, including advanced threat detection, encryption, and continuous monitoring, Sify ensures that enterprise data remains secure. Additionally, Sify’s expertise in regulatory compliance helps businesses adhere to industry standards and regulations, mitigating risks and ensuring peace of mind.
Optimized Performance and Cost Efficiency
Managing performance and costs effectively is critical in a multi-cloud setup. Sify’s Multi Cloud Managed Services include comprehensive monitoring and optimization to ensure that resources are utilized efficiently and performance is maximized. By analyzing usage patterns and deploying cost-saving strategies, Sify helps businesses reduce unnecessary expenses while maintaining high levels of performance. This approach not only enhances operational efficiency but also delivers significant cost savings.
Disaster Recovery and Business Continuity
In today’s fast-paced business environment, ensuring continuous availability and rapid recovery from disruptions is essential. Sify’s Multi Cloud Managed Services include robust disaster recovery and business continuity solutions. By leveraging the strengths of multiple cloud platforms, Sify ensures that businesses have resilient and redundant systems in place, minimizing downtime and ensuring quick recovery in the event of a disaster.
Future-Proofing with Innovation
Sify’s commitment to innovation and continuous improvement ensures that their clients remain ahead of the curve in the ever-evolving cloud landscape. By staying at the forefront of technological advancements and industry trends, Sify helps businesses adapt to new challenges and opportunities. Whether it’s adopting emerging technologies or optimizing existing processes, Sify’s Multi Cloud Managed Services provide a future-proof foundation for digital transformation.
Sify Technologies’ Multi Cloud Managed Services empower businesses to navigate the complexities of multi-cloud environments with confidence and ease. With a focus on seamless integration, enhanced security, optimized performance, and cost efficiency, Sify enables enterprises to unlock the full potential of their multi-cloud strategies. By partnering with Sify, businesses can achieve greater agility, innovation, and growth, ensuring they remain competitive in the digital age.
0 notes